Overview
Ransomware is a specific type of malicious software that locks your computer and demands payment, typically in cryptocurrency. Clear instructions are usually provided on how to make the payment. The idea is that the attackers will send the decryption key after payment is received, as it is in their best interest to do so to maintain the credibility of their scheme and continue exploiting the same vulnerability.
In 2022, ransomware attacks resulted in over $20 billion in losses. Ransomware typically consists of two main components: the delivery mechanism and the encryption component. The encryption component recursively crawls the file system, encrypting each file individually.
In this overview, we will focus on the encryption component of ransomware rather than the delivery mechanism.
First step is to download a virtual machine. I will be using Oracles virtual box to run a virtual machine with a windows 10 ISO. You will want to run the ransomware in an isolated environment so a VM is a must.
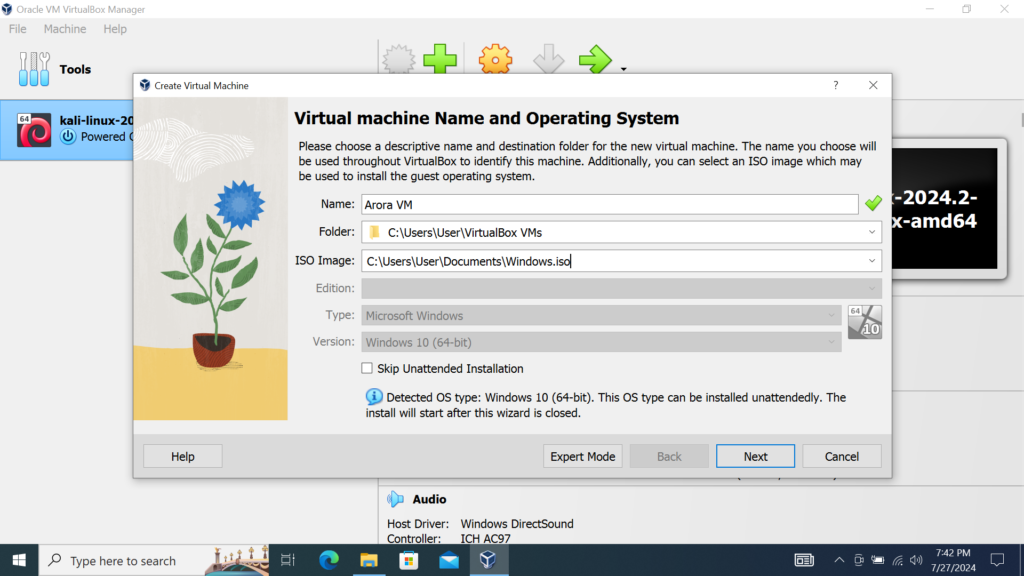
After creating the virtual machine, we need to download visual studio community with install.NET development inside the virtual machine.
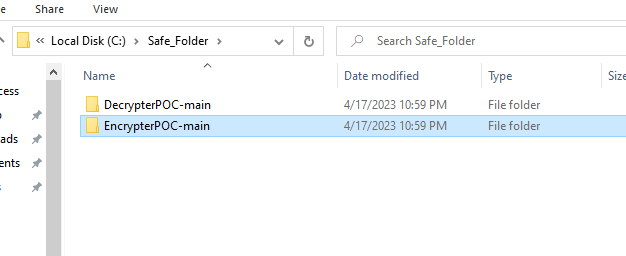
Next you have to download the ransomware code from github, there are two files the encryptor and decryptor, you must put it in a safe folder on the C drive because the encryptor will encrypt the desktop, documents, and pictures
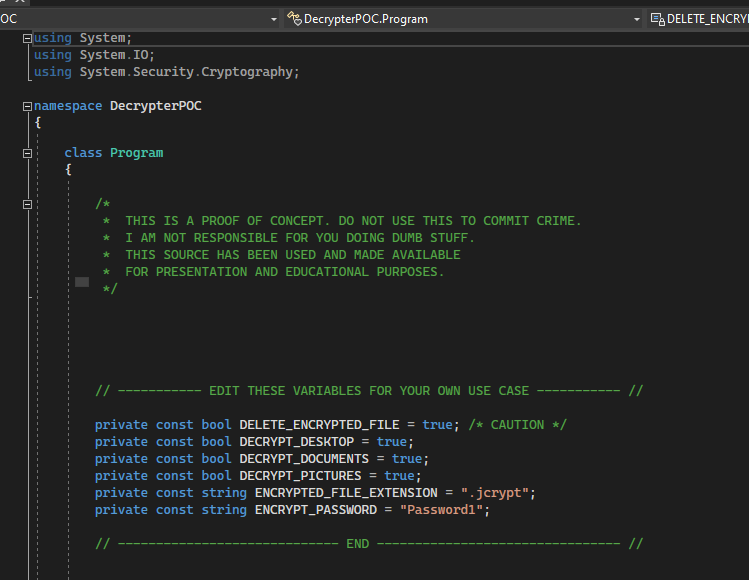
The encryptor code looks like this, you can see it on visual studio. DELETE ALL ORIGINALS TRUE means that once these files are encrypted, the original ones are deleted. The next three valuables is where you want to encrypt the files. ENCCRYPTED FILE EXTENSION, is appended to show that they are encrypted. Encryptor and Decryptor uses symmetric encryption. The next is the bitcoin address for the ransom. The email address is where you would email the transaction ID to the criminal.

The decryptor looks like this.
When you run the encryptor, your files will get encrypted. This is before encryption:
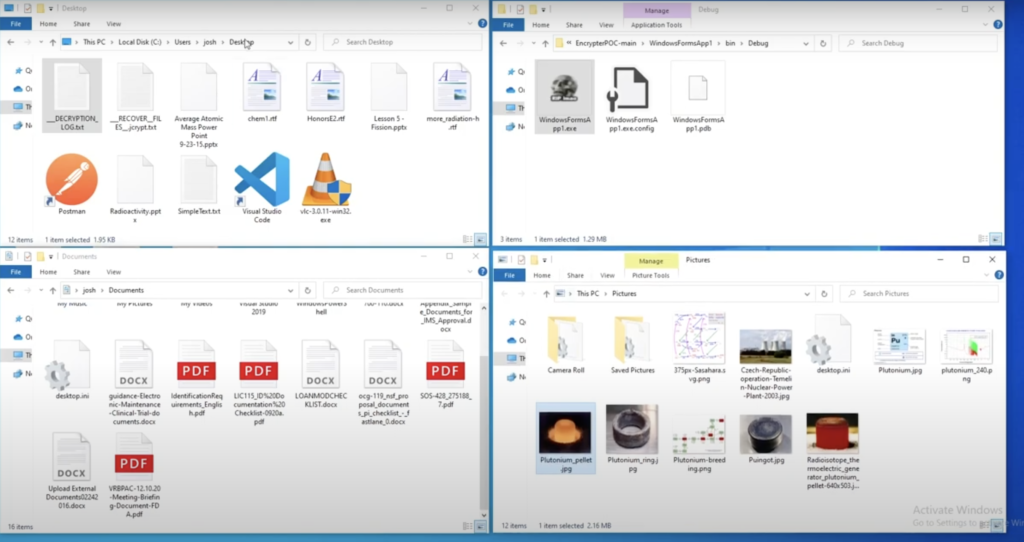
This is after encryption:

After the files get encrypted this picture comes up asking for a ransom
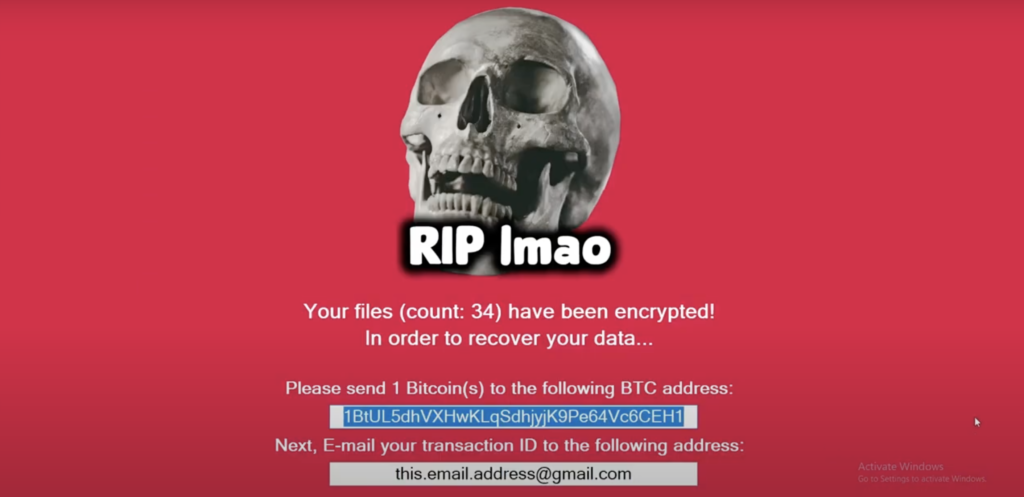
To decrypt you run the decrypt file in your safe folder in the C Drive.
Leave a Reply